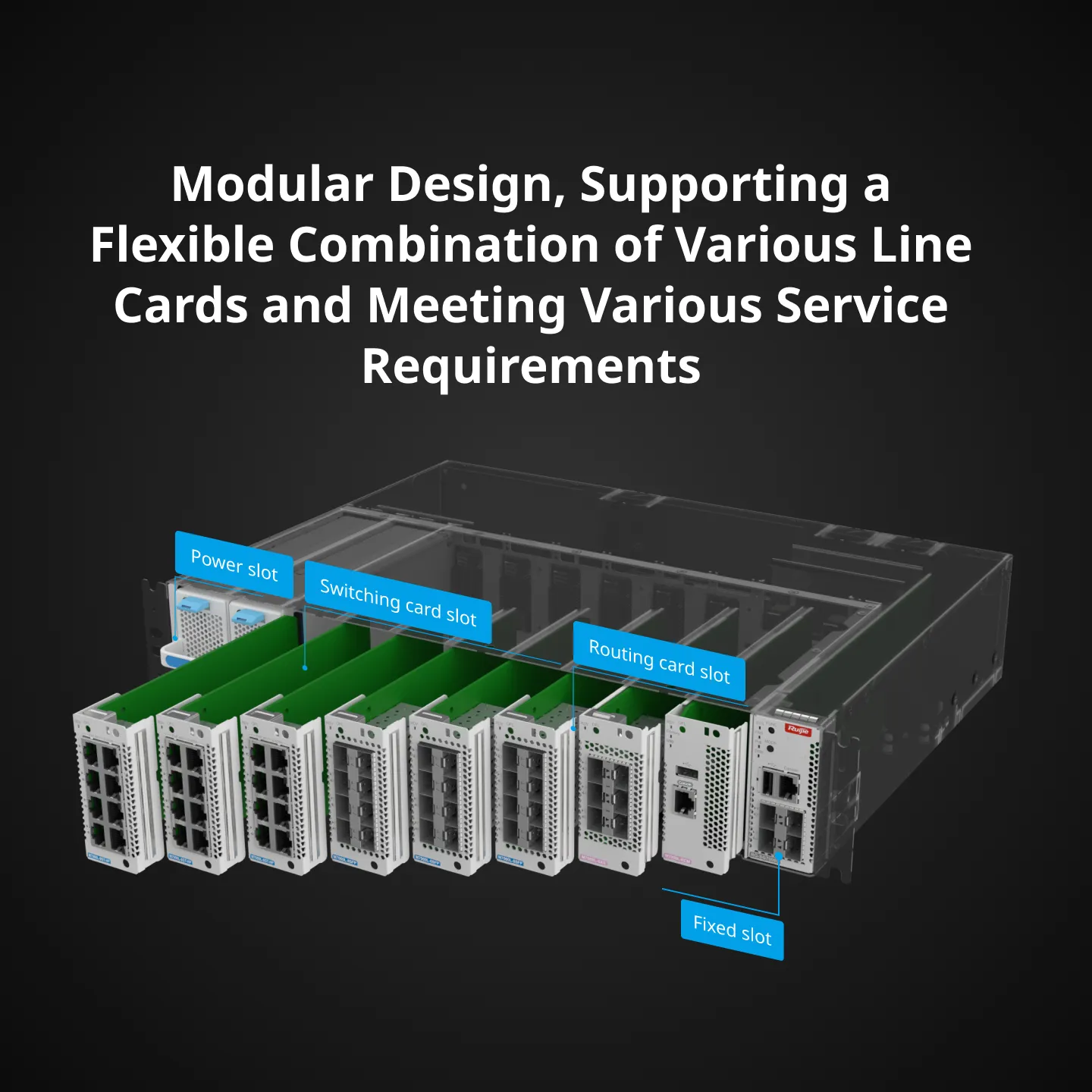
| Software Specifications |
Product Feature |
RG-SG7008L |
| Switching module |
VLAN |
4000 IEEE 802.1Q VLANs Port-based VLAN Private VLAN Voice VLAN GVRP |
| QinQ |
Basic QinQ Flexible QinQ |
| Link aggregation |
LACP (IEEE 802.3ad) |
| Spanning tree protocols |
STP, RSTP, and MSTP |
| VXLAN |
The hardware supports Virtual Extensible LAN (VXLAN). Through software upgrade in the future, a logical Layer 2 network can be built on the basis of the Layer 3 network. |
| DHCP |
DHCP server DHCP client DHCP snooping DHCP relay IPv6 DHCP server IPv6 DHCP snooping IPv6 DHCP client IPv6 DHCP relay |
| IP routing |
RIP and RIPng BGP4 and BGP4+ OSPFv2, OSPFv3, IS-ISv4, and IS-ISv6 Packet-based and flow-based load balancing |
| Multicast |
IGMPv1/IGMPv2/IGMPv3 and IGMP proxy PIM-DM, PIM-SM, and PIM-SSM MLD Snooping and MLD PIM for IPv6 |
| ACL |
Flexible and diversified hardware ACLs Standard IP ACLs (IP-based hardware ACLs) Extended IP ACLs (hardware ACLs based on IP addresses or TCP/UDP port numbers) MAC-based extended ACLs Time-based ACLs Expert-level ACLs IPv6 ACL |
| Basic security features |
3-tuple binding (IP address, MAC address, and port) Filtering of unauthorized MAC addresses 802.1x authentication based on the port number and MAC address Portal authentication and Portal 2.0 authentication ARP check, ARP packet rate limiting, gateway-targeted ARP spoofing prevention Port protection Broadcast storm suppression Hierarchical management and password protection of administrators RADIUS and TACAS+ AAA for device login management SSHv2 to provide a secure, encrypted connection for user login BPDU Guard CPP and NFPP Attack defense, DoS/DDoS defense, fragmentation attack defense, SYN attack defense, and IP spoofing attack defenseL2TP, IPsec VPN, GRE |
| Management features |
SNMP, CLI (Telnet/Console), RMON, SSH, syslog, NTP/SNTP, SNMP over IPv6, IPv6 MIB support for SNMP, SSH over IPv6, Telnetv6, FTPv6/TFTPv6, DNSv6, NTP for IPv6, and Traceroute for IPv6 CLI configurations including the console port, auxiliary port, Telnet, or SSH File transfer protocols such as FTP, TFTP, and XMODEM sFlow, which utilizes the random sampling technology to sample flow information on the traffic of a switch WIS-based management |
| High reliability |
VSU (virtualizing multiple devices into one device)
BFD
ERPS (G.8032)
REUP
RLDP
1+1 power redundancy
Hot swapping of power modules |
| Routing module |
IPv4 features |
LLDP, 802.1Q, 802.1p, 802.3ad, and other Ethernet features Static routing, RIPv1/RIPv2, OSPFv2, BGP, IS-IS, PBR, and routing policies VRRP, FTP, and TFTP ECMP and WCMP Static and dynamic NAT, static and dynamic NAPT, and VPN NAT DNS resolution and smart DNS NTP server and NTP client |
| IPv6 features |
IPv6 addressing, Neighbor Discovery (ND), ICMPv6, Stateless Auto Configuration, and Path MTU Discovery Static routing, RIPng, OSPFv3, BGP4+, IS-ISv6, ECMP, and PBR VRRPv3, BFDv6, and 6VPE IPv6 ACL, NAT64, NAT-PT, DHCPv6, DNSv6, FTPv6, and TFTPv6 Manual tunnel, automatic tunnel, ISATAP, and GRE tunnel |
| MPLS |
MPLS forwarding, MPLS VPN/VPLS MPLS VPN inter-AS option A/B/C |
| SSL VPN |
Enabled by default; supporting access on the web page and iOS, macOS, Windows, and Android clients |
| Egress features |
User management, ACE based on user groups, and rate limiting for individual users Egress routing, ISP address library, Reverse Path Limited (RPL), domain name-based routing, and multi-link load balance (MLLB) DNS proxy, reverse DNS proxy, and DNS redirect Flow table-based attack prevention, single-user session limit, flow attack log, and flow table memory optimization Configuration backup and one-click recovery Flow log and URL log |
| Security zone |
Security zone division based on the IP address Security zone division based on the logical interface Attack defense domain (global protection policies, protocol policies, and domain policies) Security audit (attack defense domain log audit, security zone log audit, and management log audit) |
| URL filtering |
Self-defined URL and URL logs Automatic remote upgrade of URL library through HTTP Local storage of logs and storage on external log servers (including NAT logs, flow logs, and URL logs) |
| Attack prevention |
ARP attack prevention LAN attack prevention and WAN attack prevention Secure address binding Port scan attack prevention Segmentation packet attack prevention ICMP flood attack prevention Smurf attack prevention Teardrop attack prevention ICMP redirect attack prevention ICMP unreachable attack prevention |
| Application Identification |
Self-developed application identification function that can identify various application types, customizable application identification protocol P2P applications Streaming media software Chat software Game software Internal enterprise applications |
| Content audit |
Email content audit IM audit BBS forum content audit Search engine audit |
| EMB module |
Device status query |
Query device details, CPU/memory usage, interface status, temperature, power supply, fan, traffic, and bandwidth utilization |
| Network configuration |
VLAN management, trunk management, port setting, aggregate port, port mirroring, port rate limiting, static routing, DHCP, DHCP snooping, STP loop guard, RLDP, and remote power supply management |
| Zero- configuration features |
CPE WAN Management Protocol (CWMP) |
| Network management configurations |
Syslog, Telnet, and SNMP |
| Diagnosis tools |
Network detection and one-click information collection |
| Operations on devices |
Upgrade, restart, configuration management, system time, log server, DNS server, system character set, and web console |
| Quick configuration |
Quick configuration |
| Operation log |
Log query, log type, and log management |
| Device upgrade |
Device upgrade |
| Administrator account |
Web administrator configuration |
| Data backup and recovery |
Data backup download, data import and recovery |